How MSPs Use IP Geolocation to Protect Clients
While traditional security measures such as firewalls, strong password policies and encryption remain crucial, their primary focus on securing network perimeters makes them less effective against location-based attacks. This is where IP address geolocation comes in. By leveraging IP data, you gain insights about the location of login attempts, allowing you to distinguish legitimate access from suspicious activity.
However, it’s important to remember that using IP geolocation data without context generates false positives, contributing to security alert fatigue — a state of information overload that numbs security professionals to even critical threats.
What Is IP Geolocation?
IP geolocation, also called “internet protocol geolocation,” is the process of approximating the geographic location of a device based on its IP address.
Internet service providers assign a unique IP address to devices connected to the internet, serving as its virtual address on the network. IP geolocation uses this address to estimate a device’s geographical location, such as a country, region, city and sometimes even a specific latitude and longitude.
Types of geolocation data
Different types of geolocation data include:
| Geolocation Data Type | Description | Example |
| Positioning or georeferencing | Determining a device’s or individual’s map-based location | Monitoring the geographical location of login attempts to a SaaS application to detect unauthorized access from unexpected regions |
| Geocoding | Looking up map-based data about locations or services | Identifying the physical location of data centers or cloud providers hosting SaaS services to ensure compliance with regional data protection regulations |
| Geotagging | Attaching location data to digital media | Embedding location metadata within documents or emails sent from a SaaS platform to trace the origin in case of a data breach or unauthorized sharing |
How Does IP Geolocation Work in SaaS Security?
Here’s an overview of how IP geolocation works to improve cybersecurity measures:
- Mapping the digital landscape: Devices connected to the internet have a unique IP address identifier. IP geolocation databases associate these addresses with approximate geographic locations based on information from internet service providers (ISPs) and other sources.
- Setting baseline behavior: Establishing baseline behaviors in the context of IP geolocation refers to the typical internet usage patterns and access by users or devices, which are considered normal within a given framework. These behaviors relate to geographic consistency, device-specific access and routine access times.
- Recognizing pattern deviations: Pattern deviation analysis supports dynamic access control policies, adjusting user access and privileges based on the geographic origin of the connection. When a user logs into a client’s system from an unexpected or unauthorized IP location, you get a security alert.
How MSPs Use IP Address Geolocation for Client Security
By gathering and analyzing data on the geolocation of IP addresses, you can:
1. Implement Geolocation-Based Access Control
By analyzing the geographic origin of IP addresses, MSPs configure security policies to restrict access to a client’s network based on the user’s location. For example, your client only wants users from North America to access certain sensitive data. By using geolocation-based access control, you ensure people outside the North America region cannot access the data.
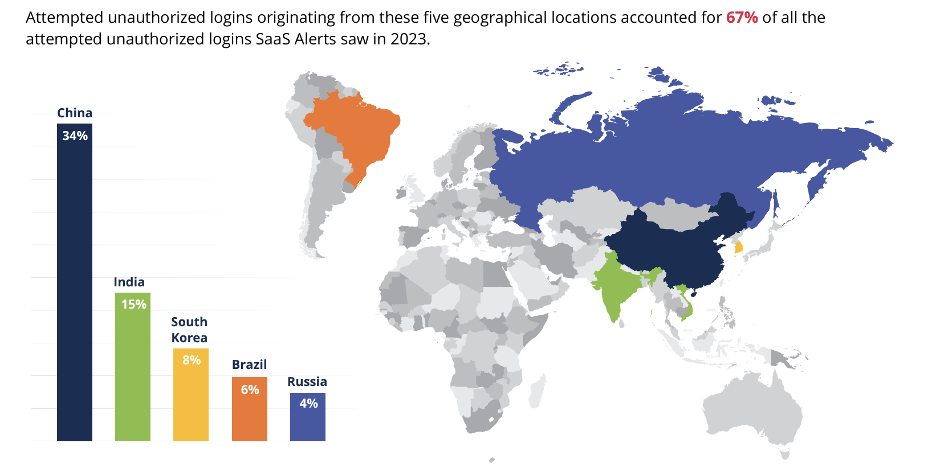
This approach mitigates the risk of intrusions from areas with high cybercrime rates. Our SaaS Applications Security Insights (SASI) 2024 report indicates that 67% of unauthorized login attempts originated from only five countries.
2. Strengthen Authentication Procedures
Multi-factor authentication (MFA) typically involves verifying user identity through multiple factors, such as passwords and one-time codes. IP geolocation data adds an additional layer by verifying the physical location of the user based on their IP address. If a user attempts to log in from an unusual or unexpected location, the system triggers additional authentication steps, adding an extra barrier against unauthorized access.
3. Improve Threat Detection
MSPs use the geolocation of an IP address to get insights into an account’s traffic patterns. This data helps track and analyze activity originating from specific geographical locations, allowing for the swift detection and response to potential threats. For instance, if traffic from a known hostile source or an unusual foreign location spikes, the system can instantly alert the MSP. This prompt response capability prevents potential breaches from escalating into full-blown attacks.
4. Streamline Compliance and Data Sovereignty
Certain compliance regulations mandate the storage and processing of data within specific geographical boundaries. If you geolocate IP addresses to identify the location of data access attempts, you can easily restrict access to data from unauthorized geographical locations, ensuring data residency compliance.
Strategies to Handle Security Alerts from Geolocation of IP Addresses
While IP geolocation enhances security measures, it also introduces the challenge of managing an influx of alerts, including false positives, which can lead to fatigue among security teams. Open Access Government reports that 83% of cybersecurity professionals are overwhelmed by security alert volumes.
To minimize alert fatigue from IP geolocation use, MSPs should:
- Allowlist safe IPs: Identify and approve a list of safe IP addresses that are regularly used by each client’s organization. You’ll want to regularly update the list of safe IP addresses and be sure to include partners and other trusted entities. This strategy reduces the number of false positives generated by security alerts from trusted sources.
- Integrate threat intelligence: Use threat intelligence platforms to correlate IP addresses with known indicators of compromise and historical attack patterns. By combining IP geolocation data with up-to-date threat intelligence, you can differentiate between benign and malicious activities more accurately.
- Adjust sensitivity and thresholds: Fine-tune the sensitivity of security alert systems and adjust thresholds based on each client’s security requirements, operational constraints and feedback from security analysts. Tailoring these settings to individual client environments allows MSPs to filter out noise while addressing critical alerts.
Leverage IP Geolocation Data with SaaS Alerts
With SaaS Alerts, MSPs get continuous insights into the geographic origin of suspicious activities to easily identify and respond to threats before they impact their clients.
Our platform strengthens your security measures by offering:
- Centralized visibility: Gain a comprehensive view of all user activity across your entire SaaS application landscape, including IP addresses and locations.
- Real-time alerts: Receive immediate notifications of suspicious login attempts or access attempts from unauthorized locations.
- Automated remediation: Take swift action to mitigate security threats, such as blocking unauthorized access attempts or suspending compromised accounts with built-in automation.
Start your free trial and discover how SaaS Alerts helps you leverage your IP geolocation data for enhanced cybersecurity.






