How to Manage the Security Risks of Guest User Accounts
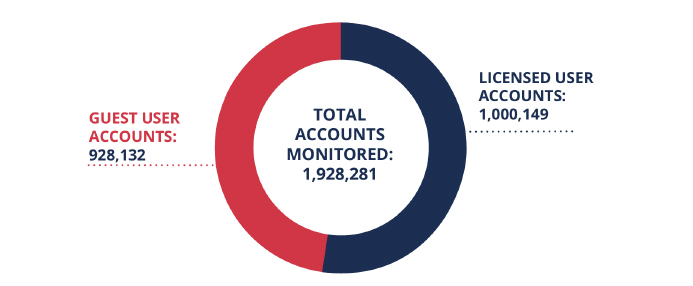
Organizations are increasingly relying on guest user accounts to facilitate external partnerships, collaborate with vendors and grant temporary access to their networks. Our SaaS Application Security Insights (SASI) report found that out of all the accounts SaaS Alerts monitors, almost half (48.1) are guest user accounts versus licensed users.
Guest accounts, though handy for collaborations and short-term access, can become a security risk when left unchecked.
Types of Guest Accounts
Knowing the types of guest user accounts helps MSPs and MSSPs implement tailored security measures for each category. Let’s take a look at the common categories of guest user accounts.
| Type | Purpose | Example |
| Vendor accounts | For external suppliers who require access to specific systems or resources | Granting access to vendors for product integrations, maintenance or support |
| Interviewee accounts | For job candidates during interviews | Granting access to online assessments or interview materials |
| Collaboration accounts | For collaboration between different organizations or teams | Giving external contributors access to shared projects |
| Beta-testing account | For beta-testing phases, allowing external users to test pre-release versions of services | Collecting feedback, identifying bugs and ensuring the product’s stability before a full release |
How Attackers Exploit a Guest User Account
Guest user accounts, if not properly managed, lead to unauthorized access to sensitive systems and, ultimately, data breaches. Understanding how bad actors exploit guest accounts allows MSPs to proactively identify and address security vulnerabilities.
Here are four common ways malicious individuals exploit guest accounts.
1. Deploying Malware Attacks
Due to the temporary and less privileged nature of guest accounts, administrators tend to configure them with weaker authentication mechanisms, such as no MFA or account lockout policies. It can be seen as a trade-off between security and user convenience to facilitate quick onboarding.
Once inside the network, attackers use the compromised guest account to deliver malware payloads. It could involve sending malicious files, links or emails containing malware to other users within the organization. Depending on the type of malware, it may have mechanisms to self-replicate or spread to other systems and devices.
2. Hijacking a Guest User Session
If the guest user’s session is not adequately protected, attackers attempt to hijack an active session to gain access without needing to know the login credentials. Guest accounts generally have longer session durations due to their temporary nature, which provides an entry point for attackers to hijack a session.
This hijacking is done through various means, such as session cookie theft or man-in-the-middle attacks.
3. Moving Laterally in the Network
After compromising a guest account, attackers use it as a starting point to move laterally within the network. They escalate privileges and target more critical systems or databases. The Global Incident Response Threat Report found that lateral movement is used in 25% of all cyberattacks.
Lateral movement is also a mechanism for pass-the-hash attacks. Instead of stealing actual passwords, attackers extract hashed password values from compromised systems. They then use these hashes to authenticate themselves on other systems within the network, bypassing the need for plaintext passwords.
4. Leveraging Stale Accounts
If guest accounts are not promptly deactivated or removed after their intended use, they remain in the system as potential targets for attackers. These stale accounts are attractive entry points for unauthorized access. Attackers, either internal or external, may use these accounts to exfiltrate sensitive data or participate in unauthorized communications, leading to potential data leakage.
Strategies for MSPs to Manage Guest Access for Security
To protect guest accounts from unauthorized access and thereby reduce the risk of data breaches, MSPs can follow these top six strategies.
1. Proactive Monitoring and Detection
MSPs should implement robust monitoring solutions to keep a close eye on guest user account activities. This approach involves continuous monitoring of log files, network traffic and system events to promptly identify any suspicious behavior or unauthorized access.
Leverage advanced tools such as security orchestration, automation and response (SOAR) systems to aggregate and correlate log data from various sources, including authentication logs, system logs and network logs.
By using SaaS security software like SaaS Alerts, you get continuous monitoring of login attempts and access patterns to instantly remediate suspicious activities.
2. Multi-Factor Authentication (MFA)
MFA acts as an additional layer of security as it requires users to provide more than one form of authentication before accessing a system. MSPs should enforce MFA solutions that support various authentication methods, such as one-time passcodes, biometrics or hardware tokens.
This extra security makes it more challenging for attackers to access resources, even if they have obtained login credentials.
3. Access Controls and Permissions
Robust access-control mechanisms, such as role-based access control (RBAC) and attribute-based access control (ABAC), ensure that guest user accounts have only the necessary access to resources and systems required to perform their specific tasks.
MSPs should also follow the principle of least privilege — allowing users the minimum level of access needed to perform their job functions. Carefully defining and restricting the permissions to sign in as guest users limits potential misuse or exploitation.
4. Session Timeouts
Set session timeouts to automatically log out guest users after a certain period of inactivity. It reduces the risk of unauthorized access in case a guest user forgets to log out or leaves a session unattended.
Configure session timeout settings in both the operating system and application levels. You can also use session management features within web applications to disable guest accounts based on inactivity.
5. Periodic Audits and Assessments
Conduct regular audits and cyber assessments of guest user accounts and their associated activities. This strategy includes reviewing account permissions, usage patterns and log data to identify and address any potential security issues.
These assessments help identify and address potential weaknesses in the security of guest accounts and associated systems.
Discover all the benefits of SaaS security assessments.
6. Remove Unnecessary Guest User Accounts
Make it a habit to regularly review log data and disable logins or delete accounts that have been inactive for 30 days or more. This helps reduce the risk of unauthorized access to accounts that have been left unattended.
Strengthen Guest Account Security with SaaS Alerts
With the specialized cybersecurity platform of SaaS Alerts, you receive instant alerts for any security incidents related to guest accounts, such as someone accessing the account from unfamiliar locations or multiple failed login attempts.
We also leverage user behavior analysis to identify anomalous patterns associated with guest user accounts, such as abnormal data transfer activities. Flagging unusual activities or deviations from established user behavior helps MSPs detect potential security threats early.
Using our Respond module, you can set up rules to automatically remove or disable guest accounts that haven’t been used over any specified time range, eliminating the need for manual audits.
Get a free trial to enhance your clients’ overall cybersecurity posture, including their guest accounts.






